Views: 1094
 0
0
 0
0
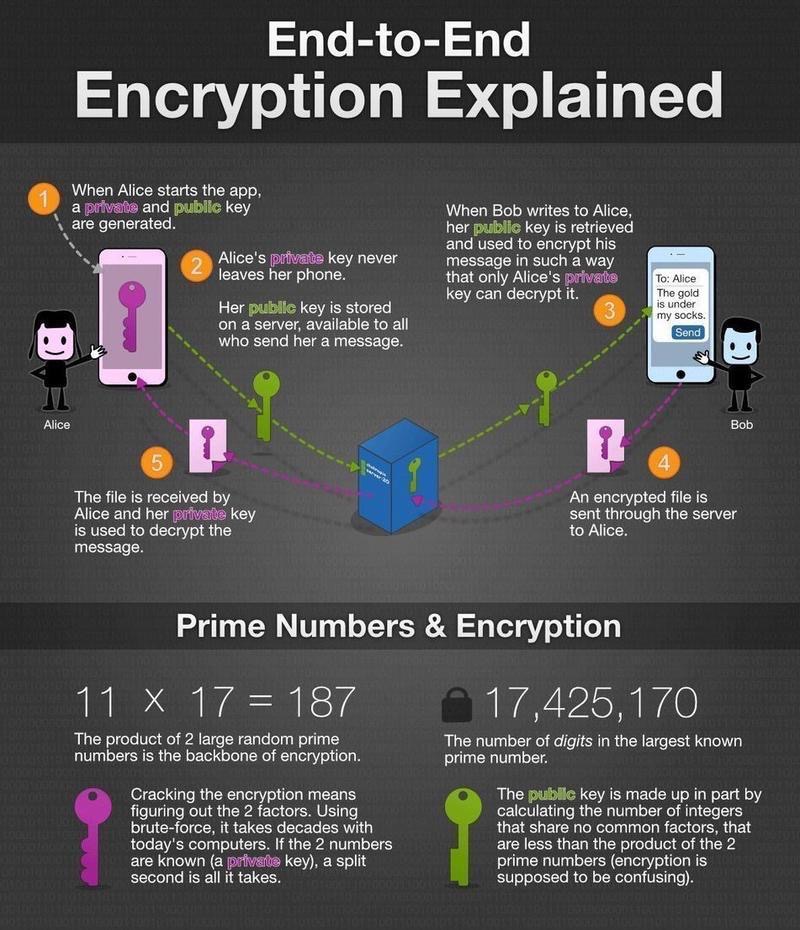
Read Time:0 Second

Início » Cibersegurança » End-to-End Encryption Explained

Um dos maiores dilemas na arquitetura de cibersegurança é o conflito entre proteção e utilidade. Historicamente, criptografar um banco de
A criptografia de dados em repouso e em trânsito resolve apenas uma fração dos riscos de privacidade modernos. No atual
No atual cenário de ameaças, confiar apenas na criptografia de repouso e de trânsito é o equivalente digital a trancar