Russian-speaking hackers have been using new malware to steal information from their victims. Called Jupyter, the threat kept a low profile and benefited from a rapid development cycle.
Although the purpose of Jupyter is to collect data from various software, the malicious code that supports its delivery can also be used to create a backdoor on an infected system.
A variant of malware emerged during an incident response engagement in October at a university in the US. But forensic data indicates that previous versions have been developed since May.
Researchers at cyber security company Morphisec found that the attack kit developers were highly active, some components receiving more than nine updates in a single month.
The latest version was created in early November, but does not include significant changes. The constant modification of the code, however, allows it to avoid detection and allows Jupyter to collect more data from compromised systems.
Jupyter is. Based on NET and focuses on stealing data from Chromium, Mozilla Firefox and Google Chrome browsers: cookies, credentials, certificates, auto-fill information.
The delivery of the thief starts with the download of an installer (Inno Setup executable) in a ZIP file that is placed as legitimate software. According to Morphisec, some of these installers have gone undetected in the VirusTotal scanning platform in the last six months.
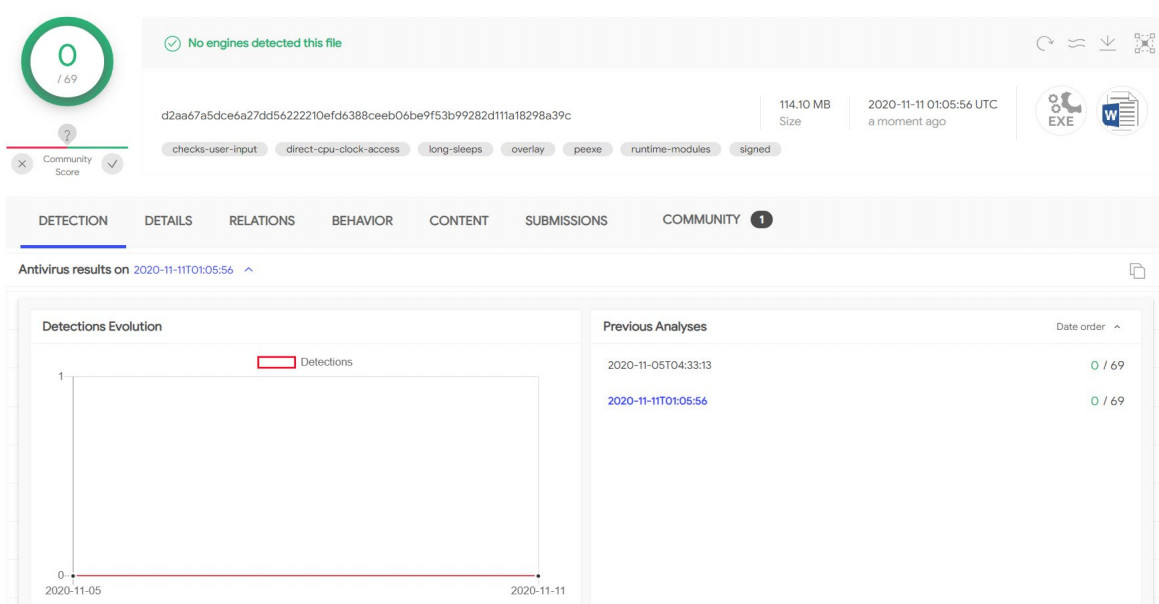
The installer takes advantage of the process coupling technique to inject a .NET loader acting as a client to the command and control server into the memory of a process.
“The client then downloads the next stage, a PowerShell command that runs the Jupyter .NET module in memory,” explainsMorphisec .
In a later version of the installer, developers switched from the process hollow to a PowerShell command to run in memory.
All of these features – the C2 client, the download and execution of malware, PowerShell scripts and commands, and the process hollowing technique – allow for extended backdoor functions.
As morphisec observed, the initial installers that initiate the attack chain present themselves as Microsoft Word documents and use the following names:
A-Tabela-Electoral Process.exe
Mathematics-Concepts-Pre-Calculation-Applications-Solutions.exe
Excel-Pay-Increase-Turotial-Bennett.exe
Travel document for emergency letter
Legitimate bait, pentest tool kit
Installers run legitimate tools like Docx2Rtf and Magix Photo Manager to create a distraction while releasing two PowerShell scripts in the background, one encoded and decoded by the other.
The latest versions of the initial installer also feature the PoshC2 structure used in penetration testing to establish machine persistence by creating a shortcut LNK file and placing it in the boot folder.
O relatório da Morphisec abrange detalhes técnicos para as ferramentas e scripts usados em um ataque jupyter, traçando a evolução dos componentes e expondo seus funcionamentos internos. Indicadores de compromisso também estão disponíveis.
Ligações russas
Os pesquisadores dizem que muitos dos servidores C2 Jupyter estavam localizados na Rússia. Um grande número deles está atualmente inativo.
O link para desenvolvedores de língua russa é mais forte do que isso, no entanto, como Morphisec notou um erro de digitação que é consistente com o nome Jupyter convertido do russo.
Outras evidências que sustentam essa teoria vieram depois de executar uma busca de imagem reversa para o painel de administração de Jupyter, que mostrou um resultado em um fórum em língua russa.
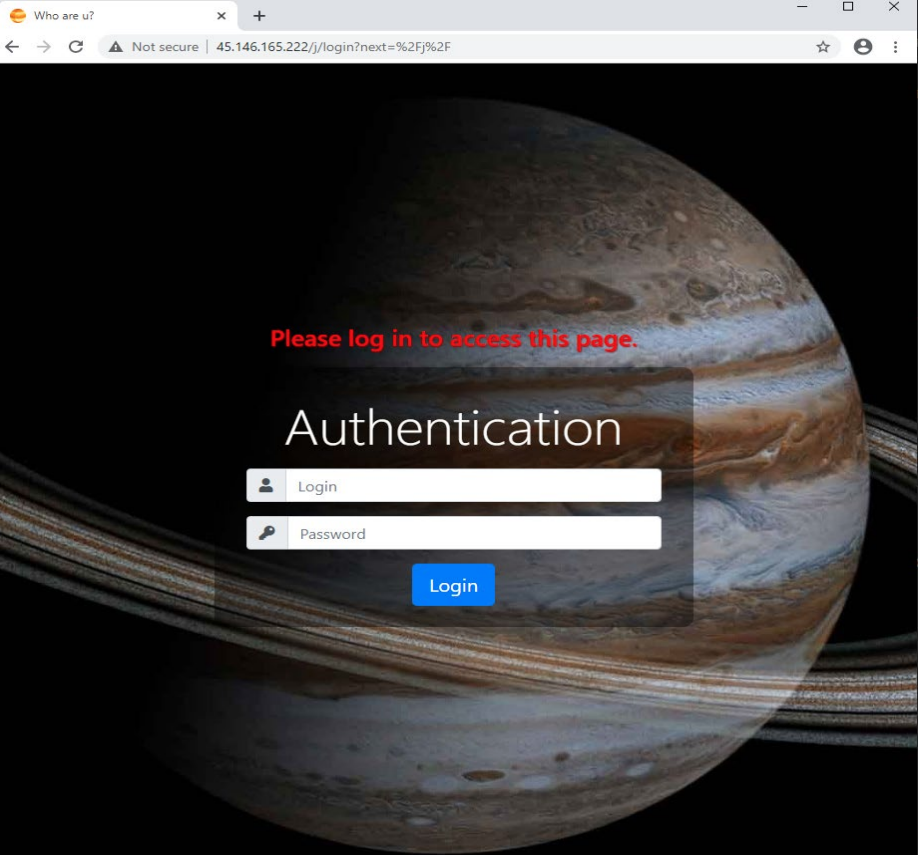
Morphisec says the constant development of this infostealer translates into adding new elements that keep it under the radar. In addition, developers expand the range of targeted information.
FONTE: BLEEPING COMPUTER
